Email authentication from Zero to BIMI
After a few months of testing, it is time to give you feedback on our journey from zero email authentication to displaying our logo in your email inbox. But before digging into details, let’s talk about what has changed since we did it.
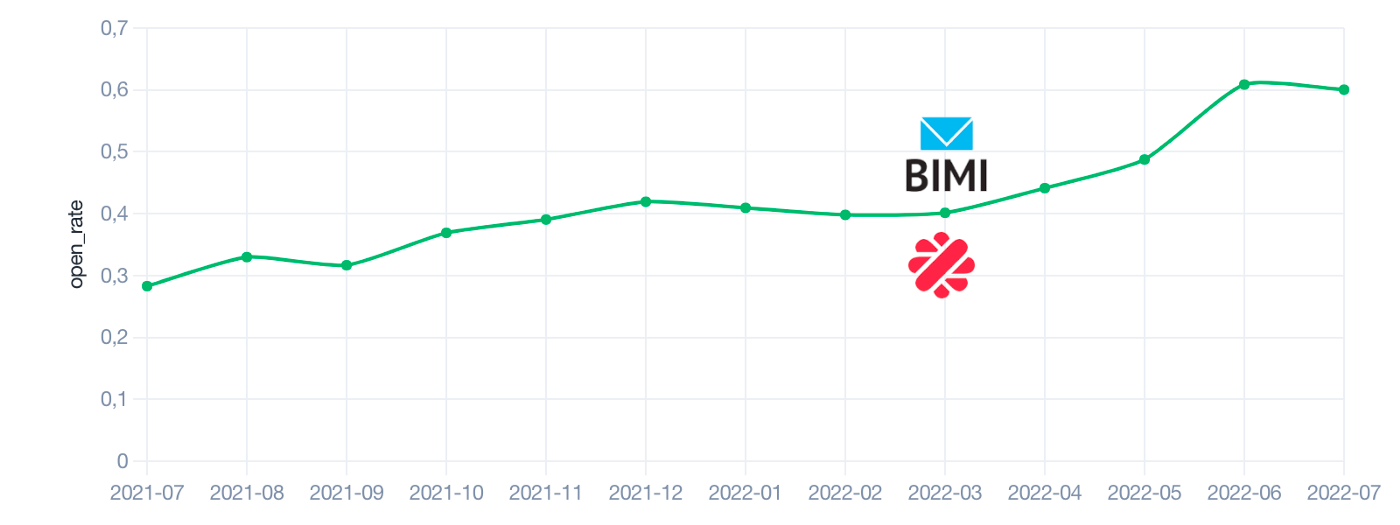
The diagram above shows the impact of displaying Malt’s logo on the open-rate of our marketing emails (sent emails / opened emails). The open rate increased directly after the logo’s appearance from 40% to 60% 🚀. This indicator helps us to evaluate our users’ commitment in relation to Malt.
To be honest, in the beginning, the BIMI feature (logo display) was not a goal in itself, but since it is here today, it is the reward for our efforts to improve the security of our emails (and also It’s very cool to have 😎, isn’t it ?)
From a security perspective, we noticed significant improvements after implementing email authentication. We don’t receive emails impersonating Malt’s employees anymore, and we have more control over Shadow IT. We control which tools are used to send emails in our behalf (I discovered in this occasion how much our sales colleagues are creative 😆)
Email authentication journey:
For Malt, like other startups/scaleups, emails are a top revenue-driving channel and our teams have various needs regarding it. Each department has its own usage that brings the need to use several tools (transactional emails, marketing emails…).
As we take security very seriously, especially when it impacts our customers, we decided to take a closer look at email security, especially outbound ones.
One of the major risks related to email security is email spoofing. It’s used in phishing attacks to make users think they have received an email from someone (your CFO for example) when they have not. It’s also a common way to install malware and ransomware.
As soon as you start looking for a solution to mitigate this issue and minimize the risk of impersonation, you’ll quickly find blog posts talking about SPF, DKIM, DMARC and BIMI.
What the heck are SPF, DKIM, DMARC and BIMI ?
Let’s take a high-level look without digging into technical details, there are many articles that explain these concepts very well.
All you need to know is that when Alice from ECorp sends an email to Bob, the email passes through the SMTP (Simple Mail Transfer Protocol) server. The SMTP is used to deliver emails from one person to another. Just with the SMTP protocol, Bob can’t be sure that it was Alice who sent him the email or that the content has not been altered. This is where additional protocols like SPF and DKIM come into action.
The configuration of these protocols is done through DNS (Domain Name Server) records.
SPF (Sender Policy Framework) is an authentication mechanism that tells the receiving server if the sender’s IP address is allowed to send an email using your domain name.
DKIM (Domain Keys Identified Mail) is another authentication mechanism. It relies on an encryption key and a digital signature that ensure that the content of the message has not been altered during transmission.
DMARC (Domain-based Message Authentication, Reporting & Conformance) is used to inform the receiver mail providers of the action to take if the email does not pass the verification process (unauthenticated email). We can tell the provider to refuse the reception of email or to put in the spam.
BIMI (Brand Indicators for Message Identification) is a new specification that displays your company’s brand logo on the receiver’s email clients. It helps your users to quickly identify your emails and assure them that the mail has not been impersonated.
How we roll it out at Malt
Like most projects, the first step was to audit and monitor the existing system to learn how it works. Fortunately everything is provided by DMARC. All we did at the beginning was to create a DMARC record with enforcement set to none and an email address to receive daily DMARC reports.
v=DMARC1; p=none; pct=100; rua=mailto:[email protected];
A few hours later, we started to receive our first reports. I really advise you to use a tool to parse these reports for you. It’s almost impossible to do it by yourself. At Malt, after a quick try to develop an in-house parser application, we decided to use DMARC Digests (Build or Buy 😃 ) . It’s easy to use and not very expensive 😛
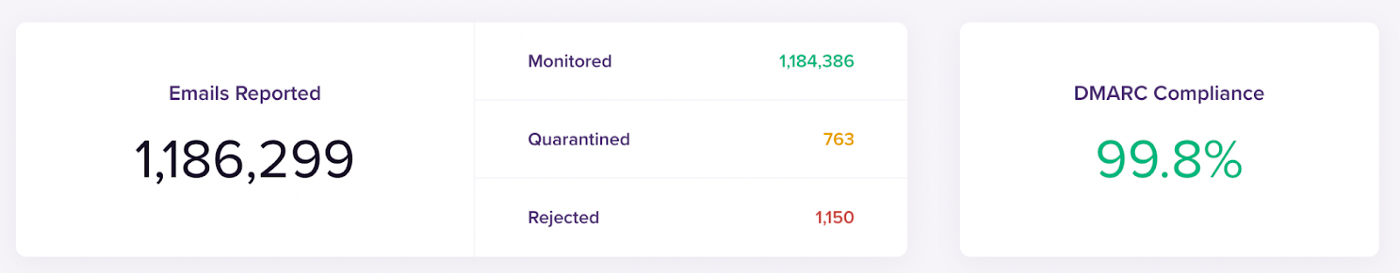
Each week, using DMARC Digest, we allocated some time to look at the reports. We identified third-party senders that are sending emails using our domain and we fixed some missing SPF/DKIM configurations. We stayed with this mode for one month.
As soon as we started to be more confident and did not detect any configuration problem for several days, we decided to move to the next step. We updated our DMARC policy from none to quarantine and gradually increased the percent of mail impacted by this policy to reduce the risk of having all our emails marked as spam (using the pct parameter). We started with pct=10%, and we went to 100 step by step in a few days. After a few months, we decided to take the last step and set the policy to reject.
At the same time, we were following the BIMI project. It was in the private beta phase, and it caught our interest. It was a good way to show that a security project can have a positive impact on a company’s business.
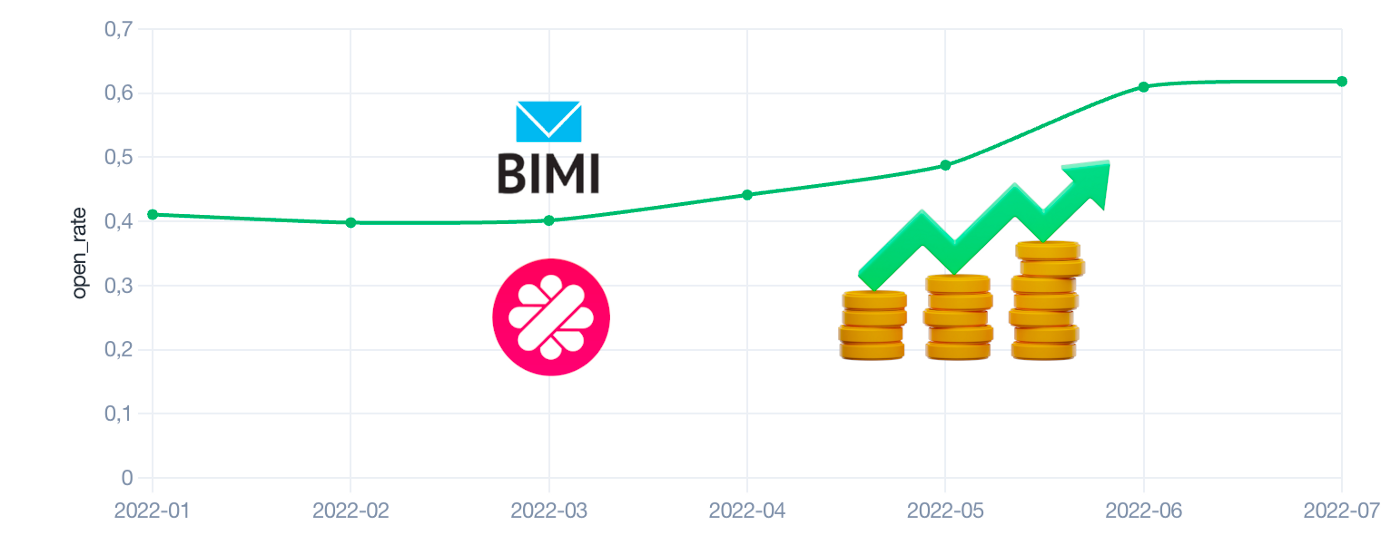
Early July 2021, as soon as Google announced that BIMI was live, we implemented it immediately. It was very easy to do except for the VMC (Verified Mark Certificate) request.
A VMC serves to prove the ownership of the logo. At the time of our request, only Entrust and DigiCert supported BIMI as certification authorities. We decided to make the request through DigiCert. There were several steps, documents to sign at the notary and two zoom meetings. It’s the first time we’ve done this kind of “complicated” process.
v=BIMI1; l=https://www.malt.com/bimi/malt.svg; a=https://www.malt.com/bimi/malt.pem;
Once the record was published with the VMC and the logo, the only thing we had to do was to wait. For us, it was long months of waiting. It took six months for our logo to appear. But again, we were very proud 😎
To conclude, implementing this kind of feature was very challenging in a growing organization with several millions of emails sent monthly. The key to success is the choice of a good tool and gradual implementation. It’s useless to go very fast. it’s a marathon not a sprint. We still have a lot of things to do concerning email security. We will keep you informed 😉